Author

Paul Halliday
Director Software Engineering
Category
Conceal Blog
Published On
Nov 6, 2025
Understanding How Conceal Protects the Browser: Part 3
Most people assume browser protection is a binary act; a URL is either blocked or allowed. But that model belongs to an older web. Today’s threats don’t live in the address bar; they live in the page itself: inside iframes, hidden inputs, scripted redirects, staged forms, delayed injections. The truth is, a malicious site can begin innocent, evolve into deception mid-session, and reveal its intent only after interaction.
That’s why the Conceal extension doesn’t react once. It observes continuously. It doesn’t ask, “Is this bad?” It continually asks, “Does everything here make sense? What is this page trying to do?”
Seeing the Page Over Time
It’s not one decision. It’s a sequence.
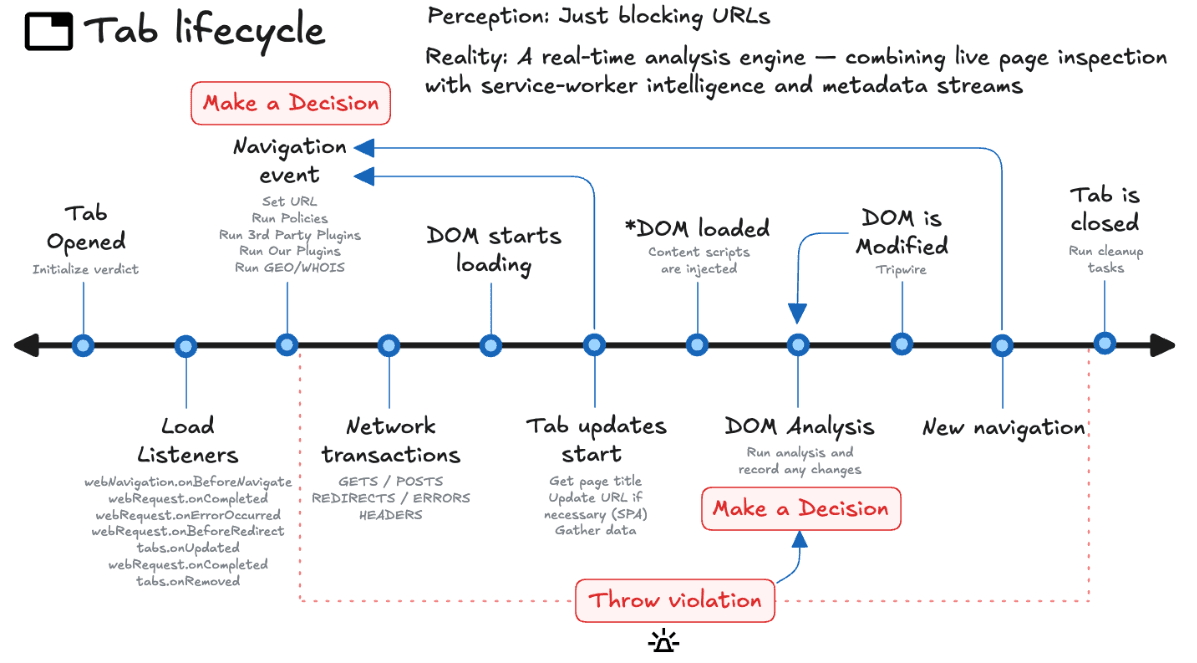
From the moment a tab opens, the extension enters a timeline, not a snapshot. A blank tab becomes a URL request, becomes a redirect chain, becomes a page load, becomes a live DOM with scripts still executing.
At each stage, our extension is silently present:
Navigation events trigger page resets and data handoffs.
Redirect chains are preserved, not forgotten; intent sometimes hides in detours.
Page load marks the start of visual analysis, not the end of evaluation.
Post-load activity (iframes, requests, late script inserts) can matter more than anything that came before.
(We’ll revisit delayed attacks in Part 4; some sites wait until the user trusts the page before springing a trap.)
Turning a Page into Evidence
We don’t see web pages. We see structured data.
Once a content script enters the page, the extension begins converting what it sees into analyzable signals. A webpage is no longer a visual surface; it is a system of elements, forms, behaviors, and links, each of which can signal intent.
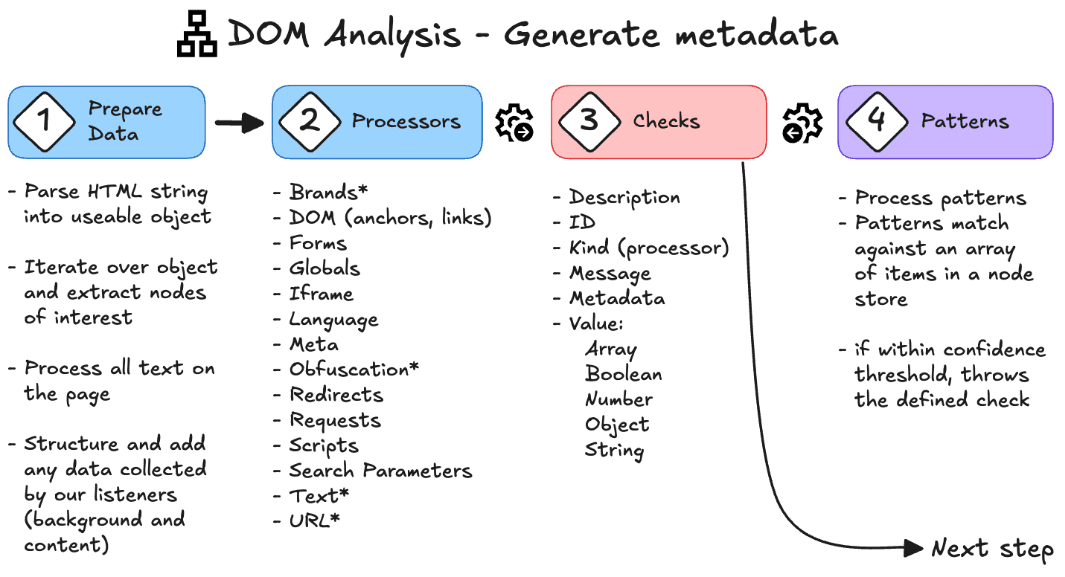
This pipeline is how a living, chaotic webpage becomes meaningful intelligence:
Preparation: We walk the DOM, collect visible and hidden elements, and merge request data or header trails passed from the service worker.
Processors: Each processor focuses on a type of signal: brands, forms, links, scripts, iframes, language hints, obfuscation patterns, redirections, and parameters.
Normalization: Everything is reduced to metadata, including key, kind, description, and value. Something we can score. Something we can trust.
At this stage, we’re not deciding. We’re listening.
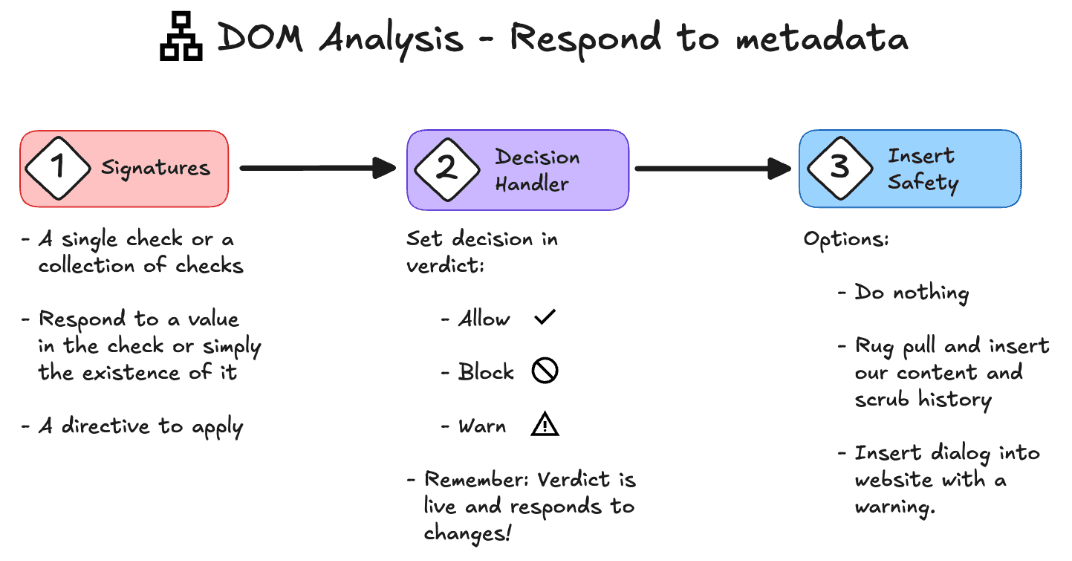
Interpreting Behavior, Not Just Structure
Evidence alone means nothing without interpretation. A login form is normal. A hidden login form inside an off-screen iframe is not. A script is fine. A script injected after user interaction may not be. In short, context matters.
This is where behavior begins to fork:
Benign signals: Align with expected purpose (e.g., a login at an actual login domain).
Inconsistent signals: Something doesn’t add up (e.g., brand imagery from one domain, a credential post to another).
Malicious patterns: Evidence of deception (hidden UI, forced redirects, staged overlays).
(This is where simple filters fail, intent isn’t in the element, it’s in the pattern. Part 4 will show examples.)
Checks vs. Signatures: How We Profile Risk
Not every red flag is an attack. Some are sloppy designs. Some are honest mistakes. That’s why our system separates Checks (small-scale facts) from Signatures (intent-level assessments).
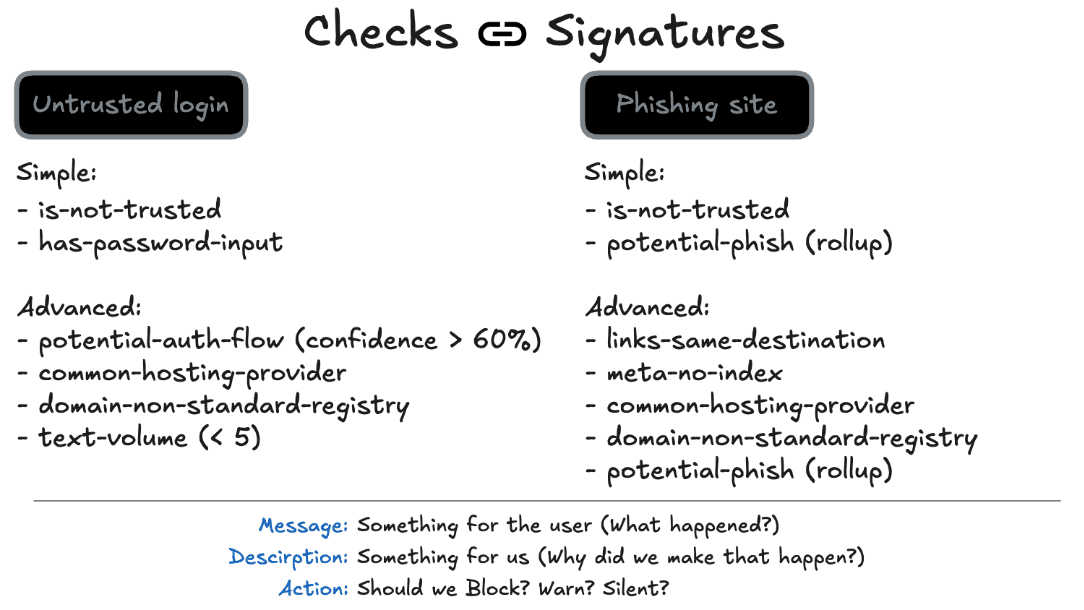
Checks are observations.
“Form posts to external domain.”
“Logo domain doesn’t match page origin.”
“Script injected after user click.”
“All links on b4nkof4merica.ru point to bankofamerica.com.”
Signatures are stories.
“This page asks for credentials using someone else’s brand.”
“This page moved the user through three redirects before presenting a form.” “This page exhibits the behavior of a login page, but structurally it does not.”
Checks create fragments. Signatures assemble narrative.
Most pages generate benign checks and never escalate to signatures. Silence, in that case, is confidence, not absence.
Quiet Judgment
Most websites pass without intervention. That doesn’t mean nothing happened. It means everything made sense. A banking login that behaves like a banking login. An e-commerce portal that behaves like a storefront. A blog that behaves like a blog.
We don’t protect by shouting. We protect by watching intent and intervening only when intent turns.
Next: The Adversaries
We’ve seen how a site becomes data, and how data becomes judgment. But what happens when a site is built to deceive? When it borrows your bank’s layout, hides its actual destination, waits for the moment of trust?
That belongs to Part 4, Tricks, Traps, and How We Fight Back, where we confront real attack strategies and show how intent reveals itself, even in silence.
To learn more about Conceal’s approach to Zero Trust Access and Real-Time Browser Security, schedule a demo today.

